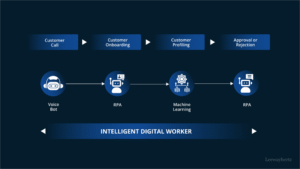
In a digital era dominated by data, alphanumeric sequences such as “001-gdl1ghbstssxzv3os4rfaa-3687053746” can appear cryptic, yet they often carry significant meaning in backend systems, file management, user tracking, and beyond. While at first glance this string may look like a randomly generated code, its structure and components suggest it belongs to a broader architecture — possibly a database identifier, a content management token, or a cloud-based asset designation. This article unpacks the possible implications, structure, and uses of such a string to better understand its role in the digital environment.
Breaking Down the Structure
The string 001-gdl1ghbstssxzv3os4rfaa-3687053746 appears to be composed of three main parts, each separated by hyphens:
-
001
-
gdl1ghbstssxzv3os4rfaa
-
3687053746
Let’s analyze each section to infer possible meanings or system uses.
The Prefix: “001”
The prefix “001” is commonly used in a wide range of technological applications. This could indicate:
-
Sequential Identification: It could be the first item in a list or batch. In databases or file systems, leading zeroes help in sorting and organizing entries efficiently.
-
Version Control: In version-controlled environments, “001” might denote the initial release or iteration of an object.
-
Location Marker: In distributed systems, “001” might refer to a specific server cluster, geographical location, or data center node.
The use of a three-digit numeric code hints at systematic classification, where additional entries would follow the format “002,” “003,” and so on.
The Core Identifier: “gdl1ghbstssxzv3os4rfaa”
This central portion of the string is the most complex and seemingly random. However, random-looking sequences often serve essential roles in digital architecture. Here are some possible explanations for this part:
-
Hashed Data: This could be the result of a hashing function applied to user data, filenames, or metadata. Hashing ensures that data is anonymized or made unique, often used in secure environments.
-
UUID or Unique Token: Systems use unique alphanumeric tokens to track and reference individual records, files, sessions, or users without exposing sensitive details.
-
Obfuscated Path or ID: In web-based applications or APIs, such strings might refer to obfuscated content paths to protect information and enhance security.
Such strings may also be generated using algorithms such as SHA-1, SHA-256, or custom token generation logic specific to a software platform.
The Suffix: “3687053746”
This trailing numeric sequence could play several roles:
-
Timestamp or Epoch: It might represent a Unix timestamp or a portion of a time-based record. For example, the number 3687053746 could correspond to a specific time or date in milliseconds.
-
User or Transaction ID: In systems tracking large-scale activity, a numeric suffix may be used to associate the token with a user ID, transaction number, or system event.
-
Checksum or Verification Number: Some alphanumeric strings include numeric values that serve as checksums to validate the integrity of the preceding data.
Depending on the system it originates from, this section could be used for backend analytics, logging, or indexing purposes.
Where You Might Encounter Such a Code
Codes like “001-gdl1ghbstssxzv3os4rfaa-3687053746” are prevalent across numerous platforms and technologies. Let’s look at a few domains where such formats are commonly used:
1. Cloud Services
In platforms like AWS, Azure, or Google Cloud, unique strings are often generated to name files, virtual machines, or instances. These identifiers allow systems to manage millions of resources without conflicts.
2. Web Content Delivery
Content delivery networks (CDNs) assign unique paths to content items such as images, scripts, or video files to ensure they are accessible, cacheable, and traceable.
3. Software Licensing and Activation
Software applications use similar alphanumeric structures for licensing keys or activation tokens. They help verify the authenticity and validity of software installations.
4. Database Systems
In distributed databases or sharded environments, such identifiers are key for indexing, retrieving, or updating entries efficiently across multiple nodes.
5. Security Tokens and Authentication
Security-focused systems use encoded strings as part of multi-factor authentication processes, session validation, or secure communications.
The Importance of Unique Identifiers
In any large-scale digital infrastructure, uniqueness is paramount. With billions of users, files, and processes occurring across the globe, systems must assign identifiers that do not clash or overlap. This is why generated strings like the one in question are so long and complex — they minimize the chances of duplication.
Moreover, such strings help in tracking and auditing. In regulatory environments (like finance, healthcare, or government), it’s essential to trace actions and data back to their origin. Identifiers allow seamless logging and referencing, improving accountability and system resilience.
Human Readability vs. Machine Usability
One thing to note is that these codes are machine-oriented rather than human-friendly. While humans prefer readable, logical names (e.g., “invoice_march_2025.pdf”), machines prioritize performance, scale, and uniqueness, leading to strings like “gdl1ghbstssxzv3os4rfaa.”
Yet, as technology advances, there’s an ongoing balance between user-friendly identifiers and system-focused codes. Some modern systems attempt to strike a balance, generating semantically meaningful yet unique identifiers — for example, combining a username with a hash (e.g., “emma-78gshh9019z”).
What Could Go Wrong?
Although helpful, reliance on complex identifiers can pose issues:
-
Data Loss: If an identifier is lost or corrupted, it may be difficult to retrieve or verify the associated content.
-
User Confusion: In user-facing interfaces, displaying such strings without context can confuse or intimidate end users.
-
Security Concerns: If identifiers encode too much information without encryption, they could be exploited (e.g., sequential tokens revealing system structure).
Hence, system designers often pair identifiers with metadata, encryption, and user-readable elements to reduce risk.
Final Thoughts
The string “001-gdl1ghbstssxzv3os4rfaa-3687053746” may look like a meaningless chain of letters and numbers, but its structure hints at intentional design. Whether it’s part of a file storage system, an authentication token, or a content delivery pathway, such identifiers are crucial for modern digital operations. They enable scale, organization, and security — acting as the silent framework behind everything from cloud storage to app access.

:max_bytes(150000):strip_icc():focal(749x0:751x2)/the-agency-102424-1-811561fa7e704dab9eebee5e7b36fa5a.jpg)